Topics discussed in this article:
- ACS – Azure Access Control service on SharePoint;
- Azure AD app-only model vs SharePoint app-only authentication model ;
- set-spotenant -DisableCustomAppAuthentication $false;
- set-spotenant -DisableCustomAppAuthentication $true
- Certificate-based authentication vs Secret-based authentication
Disable SharePoint-Apps only principal
What if you disable SharePoint-Apps only principal (i.e. ‘set-spotenant -DisableCustomAppAuthentication $true’ )?
Here are our test results
| app registered | permissions provided via | permissions | Auth | Disable Custom App Authentication | Connect-PnPOnline | Get-PnPTenant |
| SPO | SPO | Tenant FullControl | secret | TRUE | ok | 401 |
| Azure AD | SPO | Tenant FullControl | secret | TRUE | ok | 401 |
| Azure AD | Azure AD | MG/SP: Sites.FullControl.All | secret | TRUE | ok | 401 |
| SPO | SPO | Tenant FullControl | cert | TRUE | ||
| Azure AD | SPO | Tenant FullControl | cert | TRUE | ok | 401 |
| Azure AD | Azure AD | MG/SP: Sites.FullControl.All | cert | TRUE | ok | ok |
| app registered | permissions provided via | permissions | Auth | Disable Custom App Authentication | Connect-PnPOnline | Get-PnPTenant |
| SPO | SPO | Tenant FullControl | secret | FALSE | ok | ok |
| Azure AD | SPO | Tenant FullControl | secret | FALSE | ok | ok |
| Azure AD | Azure AD | MG/SP: Sites.FullControl.All | secret | FALSE | ok | 403 |
| SPO | SPO | Tenant FullControl | cert | FALSE | ||
| Azure AD | SPO | Tenant FullControl | cert | FALSE | ok | 401 |
| Azure AD | Azure AD | MG/SP: Sites.FullControl.All | cert | FALSE | ok | ok |
“MG/SP” means API permissions were provided via Microsoft Graph and they are Microsoft Graph API and SharePoint API
Permissions provided via SPO means an “appinv.aspx” page was used.
Finally,
when DisableCustomAppAuthentication is set to $false (i.e. SharePoint app-only service principals are enabled, as it was by default before Aug/Sep 2020),
you cannot use Azure AD app with Azure AD provided API permissions with secret, and
you cannot use Azure AD app with SPO-provided permissions with certificate…
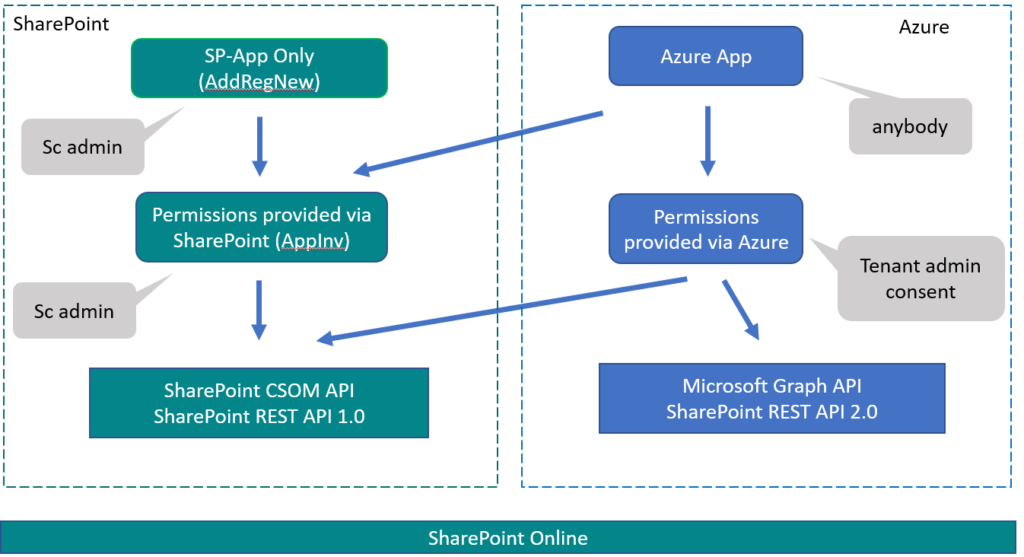
SharePoint Online Authentication/Authorization diagram:
Connect to SharePoint Online from code
How do you connect to SharePoint from code?
Option 1 (classic)
Use SP-App Only service principal: register an app via AppRegNew.aspx page in SharePoint and get AppId (Client Id) and AppSecret (client secret).
Then provide permissions to your App: use AppInv.aspx page and specify permission as an XML. Then consent (approve it) – click “Trust It” on the next page.
Option 2 (modern):
Register an app via Azure App registrations and get Application (client) ID. Generate Client Secret and/or upload Certificate.
Add API permissions you need and ask tenant admin for consent.
Option 3 (hybrid):
Register an app via Azure App registrations and get Application (client) ID. Generate Client Secret and/or upload Certificate.
Then go to SharePoint online AppInv.aspx page and provide permissions to your App via XML. Then consent (approve it) – click “Trust It” on the next page.

Pingback: Track SharePoint App-only Service Principals in Microsoft 365 ⋆ Vladilen
Pingback: Access SPO Site Programmatically via MS Graph API and SharePoint API
Pingback: SharePoint AppRegNew.aspx and AppInv.aspx ⋆ Microsoft 365 engineering